Assume servers are compromised
MindooDB is designed so that storage and sync infrastructure can be untrusted. Three independent encryption layers protect data confidentiality. Cryptographic signatures prove authorship and prevent tampering. Even a complete server breach yields only ciphertext and public keys — no plaintext data, no private keys, no usernames.

Three independent encryption layers
MindooDB's sync protocol provides defense in depth through multiple protection layers. Even if one layer is compromised, the others continue to protect data confidentiality. This is the architectural centerpiece of MindooDB's security: you don't need to trust any single layer to be safe.
Before an entry ever enters the store, its payload is encrypted with a symmetric key (AES-256-GCM). This encryption is part of the data model, not the transport. The server storing entries cannot read their contents — it only sees encrypted bytes.
When the server responds to a sync request, it wraps entry payloads in an additional RSA encryption layer using the requesting user's public key. Even if an attacker captures the HTTP response, they cannot decrypt without the recipient's private RSA key.
All communication happens over TLS. This protects metadata (entry IDs, timestamps, request parameters) that is not covered by the payload encryption layers. Together, the three layers ensure complete data protection at rest, in transit, and on the wire.
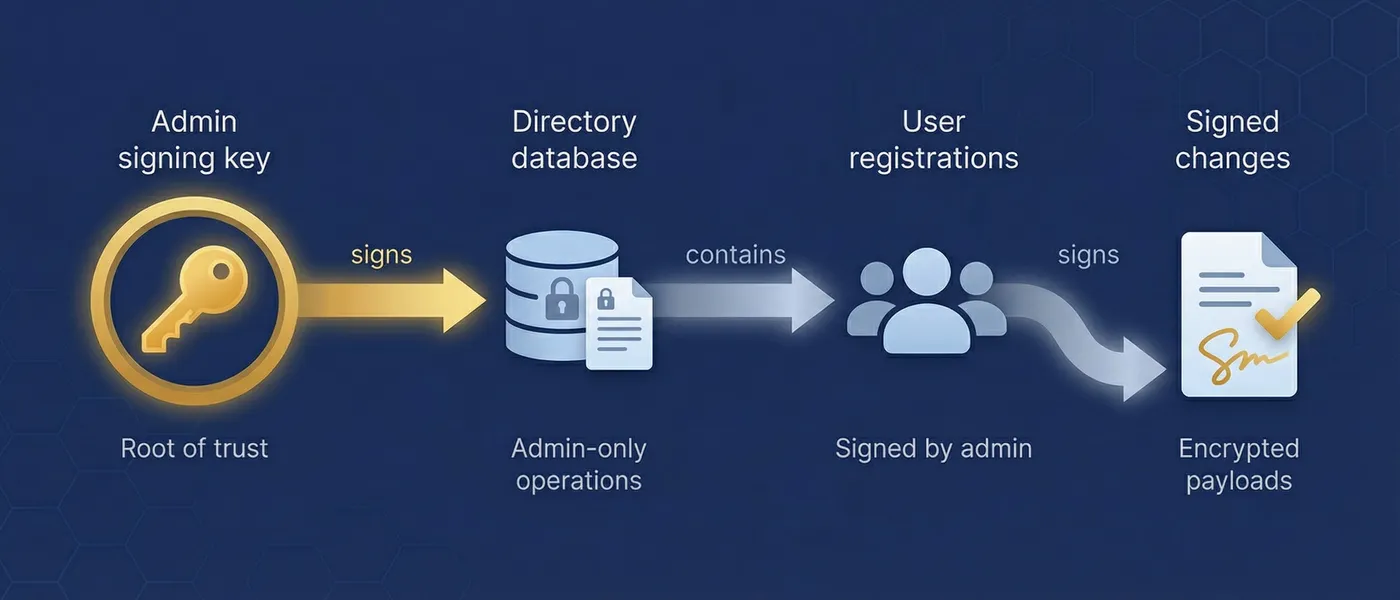
How trust is established
Trust in MindooDB flows from a single root: the admin's Ed25519 signing key. The admin signs the directory database, which contains user registrations. Every user's public key is recorded in a directory entry signed by the admin. When a client or server receives a document change, it verifies the signer's public key against the directory — if the key isn't registered, the change is rejected. No server authentication is needed; trust is established through cryptographic proofs.
What the server sees vs. doesn't see
This is the practical consequence of the zero-trust architecture. A server (or any intermediary, including relay nodes) only ever handles encrypted data and public information. Everything sensitive stays on client devices.
- Public signing keys (Ed25519)
- Public encryption keys (RSA-OAEP)
- Encrypted blobs (AES-256-GCM ciphertext)
- Entry metadata (timestamps, content hashes)
- Username hashes (SHA-256 — not actual usernames)
- Document content (end-to-end encrypted)
- Usernames (encrypted with admin RSA key)
- Private signing or encryption keys
- Symmetric encryption keys (tenant or named)
- Shared passwords (out-of-band only)
Encryption-based access control
MindooDB enforces access control through encryption keys, not server-side permissions. If you have the key, you can decrypt the document. If you don't, the document is ciphertext. This means access control works identically whether the data is on a server, a peer device, or a relay node that cannot read it.
All documents are encrypted with the tenant's default AES-256 key unless another key is specified. Every registered user receives this key during onboarding. Use for general tenant-wide data.
For sensitive documents, create a named encryption key and share it only with authorized users. Keys are distributed offline (email the encrypted key, share the password by phone or in person). Only users with the key can decrypt.
A special key that encrypts only directory access-control entries (user registrations, revocations, groups). Servers use this to validate which signing keys are trusted — without seeing usernames or business data. Usernames are stored as SHA-256 hashes; actual names encrypted with the admin's RSA key.
| Operation | Enforced by |
|---|---|
| User registration | Admin signature required (Ed25519) |
| Document creation | Must have encryption key (default or named) |
| Document modification | Must have signing key (registered user) + encryption key |
| Document reading | Must have decryption key |
| User revocation | Admin signature required; blocks sync and rejects future changes |
Challenge-response authentication and secure onboarding
MindooDB does not use passwords or tokens stored on the server. Authentication is based on Ed25519 challenge-response: the server generates a random challenge, the client signs it with its private key, and the server verifies the signature against the registered public key. This proves identity without sharing secrets.
Every sync session starts with a challenge-response handshake:
- Client sends its public signing key to the server
- Server looks up the key in the directory and sends a random challenge
- Client signs the challenge with its private key
- Server verifies the signature, checks revocation status, issues a short-lived JWT
No passwords or session databases on the server. A revoked user cannot even start the auth flow.
New users join through a three-step handshake where private keys never leave the device:
- Join request — New user generates keys locally, creates a request containing only public keys. Safe to share via any channel.
- Admin approval — Admin registers user in directory, encrypts symmetric keys with a one-time share password.
- Split-channel exchange — Join response sent via email/chat; share password communicated separately by phone or in person.
Algorithms and guarantees
MindooDB uses well-established, widely-audited cryptographic algorithms. No custom cryptography. The algorithm choices balance security strength with cross-platform compatibility (Node.js, browsers, React Native).
- Signing: Ed25519 (128-bit security, elliptic curve)
- Payload encryption: AES-256-GCM (256-bit security)
- Transport encryption: RSA-OAEP with SHA-256 (3072-bit keys)
- Key derivation: PBKDF2 with unique salts per key type
- Token signing: HMAC-SHA256
- Hashing: SHA-256 (content addressing, username privacy)
- Confidentiality: AES-256-GCM encryption — only key holders can read
- Authenticity: Ed25519 signatures — proves who created each change
- Integrity: Hash chaining — tampering breaks the chain, detectable at any point
- Non-repudiation: Signatures are unforgeable — authorship is provable
- Privacy: Usernames hashed and encrypted — server cannot identify users
What the system defends against
MindooDB assumes that servers, network infrastructure, and even some peers may be compromised or malicious. The security model is designed to maintain data confidentiality and integrity under these conditions.
- Server breach — Attacker gets ciphertext and public keys only. No plaintext, no private keys, no usernames.
- Network interception — Three encryption layers protect data even if TLS is compromised.
- Unauthorized changes — Every change is signed; unsigned or incorrectly-signed changes are rejected.
- Tampering — Hash chaining makes any modification detectable.
- Revoked user access — Revocation enforced at both challenge and token validation; blocks sync immediately.
- Relay eavesdropping — Relay nodes store and forward encrypted entries they cannot decrypt.
While payload content is always encrypted, some metadata is visible to the server by design. This is a deliberate tradeoff: the sync protocol needs metadata to reconcile entries.
- Visible: Entry timestamps, content hashes, document structure (how many entries per document), access patterns (when users sync)
- Not visible: Document content, usernames, encryption keys, attachment contents
Content hashes reveal when two entries contain identical encrypted data (for deduplication). This is an accepted tradeoff for storage efficiency.
What you should know
MindooDB is alpha software with a strong cryptographic foundation. A comprehensive security audit has been conducted, identifying areas that need hardening before production deployment. We believe transparency about limitations builds more trust than marketing claims.
Revoking a user blocks all future sync and rejects their future changes. However, previously synced data on their local device remains accessible — no system can guarantee deletion on a device that never reconnects. Mitigation: use named keys for sensitive documents (smaller blast radius), rotate keys when users leave.
Multiple keys per user (signing, encryption, named symmetric keys) require secure distribution. Mitigation: a single password unlocks all keys via PBKDF2 with different salts. The KeyBag provides unified key storage. The join request/response flow handles key exchange for new users.
By default, the server cannot query document content because it only sees ciphertext. All querying happens client-side through incremental indexing. However, if your use case requires server-side processing (e.g. an online booking system or a public website), you can give the server process a decryption key or share a subset of data with it. This is a conscious architectural choice per deployment — the default is confidentiality, with opt-in server access where needed.
A comprehensive security audit identified areas for hardening: rate limiting on endpoints, JWT token revocation, admin key rotation, and revocation timestamp protection. The cryptographic foundation (Ed25519, AES-256-GCM, RSA-OAEP) is solid. Operational hardening is in progress.
Technical controls that support compliance
MindooDB provides cryptographic building blocks that address key technical requirements of common regulatory frameworks. Compliance itself is an organizational responsibility — MindooDB gives you the technical foundation.
- ✅ Complete write history (append-only)
- ✅ Cryptographic signatures (authorship proof)
- ✅ Tamperproof records (hash-chained)
- ✅ Time travel (reconstruct any state)
- ✅ End-to-end encryption (server can't decrypt)
- ✅ Fine-grained access control (named keys)
- ✅ Coordinated data erasure (
purgeDocHistory) - ⚙️ Read-access logging (you build at app level)
These controls support HIPAA (healthcare), SOX (financial), GDPR (data protection), and PCI-DSS (payments) programs. View detailed compliance documentation →